
Cybersecurity company Kaspersky has raised the alarm and warned enterprises to beef up their cyber defenses as increasing ransomware attack in 2020 particularly in the Asia Pacific (APAC) region has evolved to become the most prevalent form of cyberattack than in any comparable period.
In a statement, Kaspersky said there was an re-emergence of two notorious ransomware groups, REvil and JSWorm, targetting victims in Asia Pacific last year, with 2020 being dubbed the year of ‘Ransomware 2.0’
Just as the name implies, ransomware is a type of malware that encrypts a victim’s data, holding it ‘hostage’ and demanding a ransom from the victim to restore access to the data upon payment.
Ransomware 2.0 according to Kaspersky goes beyond keeping a company’s data hostage, it moved on from encrypting the data to extracting a copy of the data and using it for blackmail purposes, and threatening to publish the extracted copy unless a payment is made to delete the data.
Alexey Shulmin, lead malware analyst at Kaspersky said, “2020 was the most productive year for ransomware families who moved from hostaging data to exfiltrating data, coupled with blackmailing. It is almost always a targeted ransomware.
“In APAC, we noticed an interesting re-emergence of two highly active ransomware groups, REvil and JSWorm. Both resurfaced as the pandemic raged in the region last year and we see no signs of them stopping anytime soon.
“The aftermaths of a successful attack include significant monetary loss and damaging reputation loss.”
According to the statement, Kaspersky first wrote about REvil ransomware in July 2019. Also known as Sodinokibi and Sodin, this group targeted only 44 corporate customers globally last June 2020 but had accelerated their attacked since. As a result, Kaspersky solutions protected 877 users in July 2020, logging a 1,893% increase in a span of just one month.
In addition, expert monitoring also showed the group has actively spread their malicious arms from the Asia Pacific (APAC) to the world.
“Back in 2019, most of their victims were only from APAC, particularly in Taiwan, Hong Kong, and South Korea. But last year, Kaspersky has detected their presence in almost all countries and territories. It is safe to say that during their ‘silent months’, REvil creators took their time to improve their arsenal, their method of targeting victims and their network’s reach,” said Shulmin.
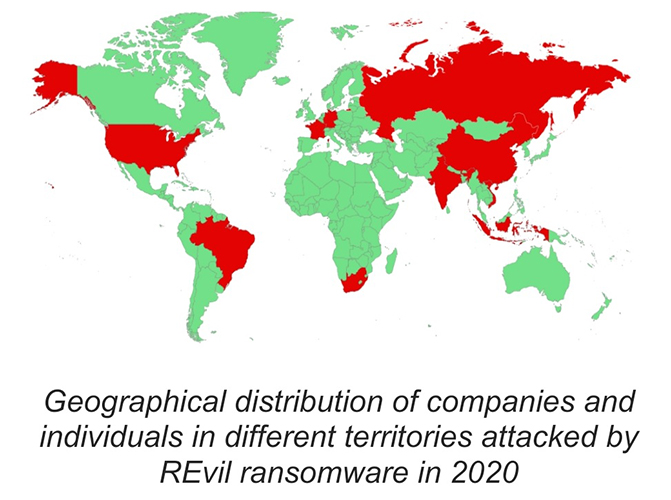
Out of 1,764 Kaspersky users targeted by the group in 2020, 635 (36%) of these companies were from the APAC region.
Brazil logged the highest number of incidents across APAC, followed by Vietnam, South Africa, China, and India.
In terms of industries, Kaspersky experts were able to categorise the group’s targets into several industries, with the biggest chunk in engineering and manufacturing at 30%, and followed by finance (14%), professional and consumer services (9%), legal, IT and telecommunications (7%) and food and beverage (7%).
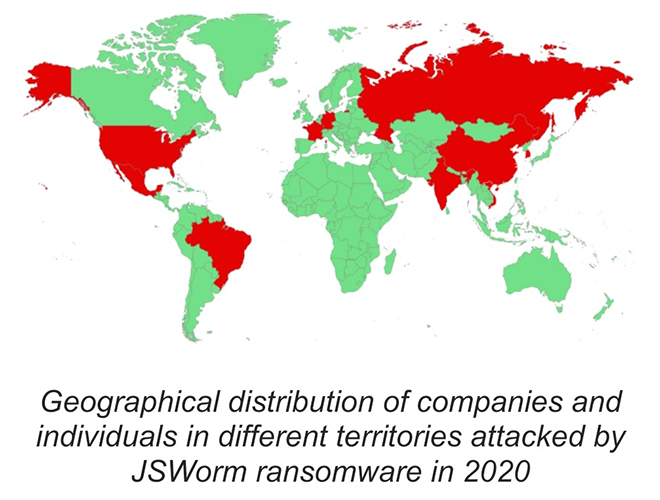
The statement also said that JSWorm, like REvil, entered the ransomware landscape in 2019. During its first months, it was detected across the globe, including in North and South America (Brazil, Argentina, USA), in Middle East and Africa (South Africa, Turkey, Iran), Europe (Italy, France, Germany), and in APAC (Vietnam).
The number of JSWorm victims is relatively lower compared with REvil but this ransomware family is gaining ground. Kaspersky solutions have blocked attempts against 230 users globally, which is a 752% increase compared with 2019’s with only 27 users infected.
Experts from Kaspersky noticed a shift of the group’s attention towards the APAC region. China emerged as the country with most number of KSN users almost infected by JSWorm, followed by USA, Vietnam, Mexico, and Russia. More than one-third (39%) of all the targeted enterprises and individuals this group were also located in APAC.
In terms of industries, it is clear that this ransomware family eyes critical infrastructure and major sectors across the world, including engineering and manufacturing (41%), followed by energy and utilities (10%), finance (10%), professional and consumer services (10%), transportation (7%) and healthcare (7%).
The JSWorm is also known by its Nemty, Nefilim, Offwhite, Fusion, Milihpen and other variants.
To remain protected against Ransomware 2.0, Kaspersky experts suggest enterprises and organisations to:
- Keep all operating systems (OS) and software patched and up to date.
- Train all employees on cybersecurity best practices while they work remotely.
- Only use secure technologies for remote connection.
- Carry out a security assessment on your network.
- Use endpoint security with behavior detection and automatic file rollback, such as Kaspersky Endpoint Security for Business.
- Never follow demands of the criminals. Do not fight alone – contact law enforcement, CERT and security vendors.
- Follow the latest trends via premium threat intelligence subscriptions.
- Know your enemy: identify new undetected malware on premises with malware analysis tools such as Kaspersky Threat Attribution Engine.







