The ongoing pandemic has led to a rapid digitalization of the healthcare sector. However, this rapid digitalization has created new security risks to patient care and private data.
Recent Kaspersky research found that 91% of global healthcare providers have implemented telehealth capabilities such as remote patient monitoring, which is done using wearable devices and monitors, and gadgets that can continuously or at intervals track a patient’s health indicators, such as cardiac activity.
Most of the wearable devices track both health data, location and movements of patients. This opens up the possibility of not just stealing data but also potentially stalking.
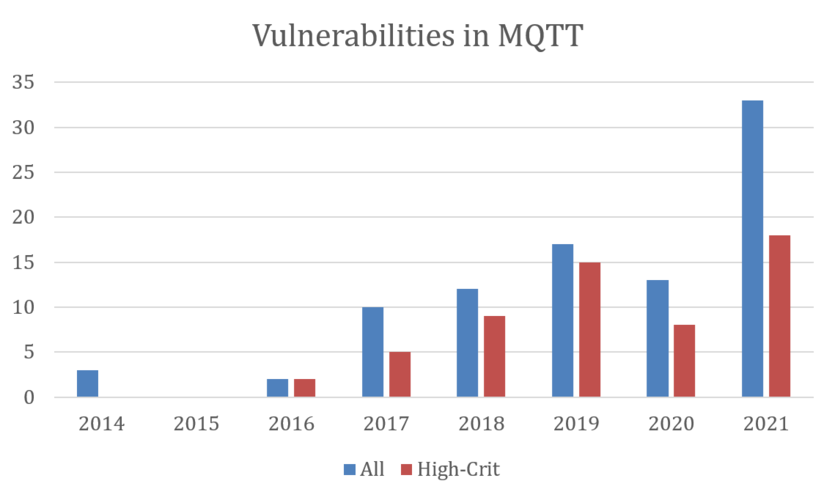
Kaspersky has discovered 33 vulnerabilities, including 18 critical ones in 2021 alone, 10 more than in 2020, in the most commonly used protocol for transferring data from wearable devices used for remote patient monitoring.
The global cybersecurity company experts said many of these vulnerabilities remain unpatched and give attackers the potential to intercept data being sent online from the device.
The most common protocol for transmitting data from wearable devices and sensors is the MQTT (Message Queuing Telemetry Transport.) protocol because it’s easy and convenient.
However, when using MQTT, authentication is completely optional and rarely includes encryption. This makes MQTT highly susceptible to ‘man in the middle’ attacks – when attackers can place themselves between “two parties” while they communicate.
The risk here is that any data transferred over the internet could potentially be stolen. When it comes to wearable devices, that information could include highly sensitive medical data, personal information, and even a person’s movements.

Maria Namestnikova, head of the Russian Global Research and Analysis Team (GReAT) at Kaspersky said the pandemic has led to a sharp growth in the telehealth market which involve not only communicating with doctor via video software but also exposure to cyber risk.
“We’re talking about a whole range of complex, rapidly evolving technologies and products, including specialized applications, wearable devices, implantable sensors, and cloud-based databases.
“However, many hospitals are still using untested third-party services to store patient data, and vulnerabilities in healthcare wearable devices and sensors remain open. Before implementing such devices, learn as much as you can about their level of security to keep the data of your company and your patients safe,” she said.
Kaspersky researchers also found vulnerabilities in another popular platform for wearable devices: the Qualcomm Snapdragon Wearable platform. There have been more than 400 vulnerabilities found since the platform was launched; not all have been patched, including some from 2020.
To keep patient data safe, Kaspersky recommends that healthcare providers:
• Check the security of the application or device suggested by the hospital or medical organization
• Minimize the data transferred by telehealth apps if possible. Eg. don’t let the device send the location data if it’s not needed.
• Change passwords from default ones and use encryption if the device offers this.







